HomeResourcesHow to use PayoneerSecuring Your Payoneer Account
Securing Your Payoneer Account
At Payoneer, we know that we’re in the trust business, and that a large part of that trust is in knowing that your funds are safe when you work with us. Choosing a payment service is a critical decision, and while low fees, flexible payment options and other value-added services are great, these solutions must…
What is an Account Takeover?
ATO involves an attacker stealing a user’s login credentials to break into their account, where they can access private information. There are several common methods that are used to get into an account, including:- Credential stuffing – Credential stuffing involves an attacker accessing an account using stolen login details from a previous data breach.
- Social engineering – Social engineering involves a hacker posing as a site administrator or another trusted figure and convincing a user to provide their login details. Phishing emails and text messages are two of the most popular to execute a social engineering attack.
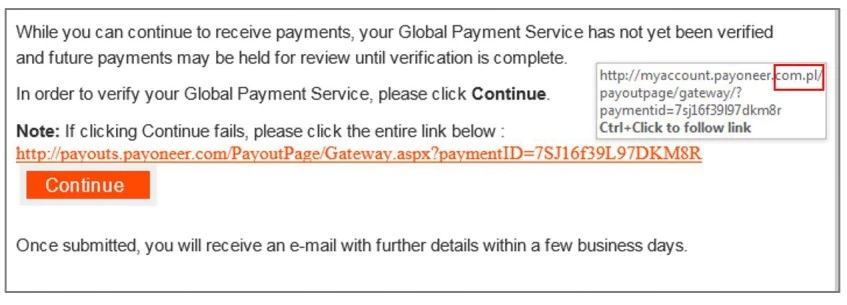
- Brute force attacks – Brute forcing is an attack in which attackers use a bot to enter a mass number of username/password combinations in a platform until an account is successfully breached.
Payoneer’s Multilayered Approach to ATO Prevention and Detection
To prevent account takeovers, we employ a number of proactive methods that keep bots and hackers from reaching a user’s account. These include:-
2-step verification (2SV) – Payoneer uses 2-step verification to help ensure that no malicious actors are able to break into your account. 2-step verification adds an extra step to certain account-related activities by sending a code to your mobile device or via phone call, which you’ll need to enter in before you can continue navigating through your account.*
- CAPTCHA requests – We use CAPTCHA challenges in several places on our system, including our login page. This prevents bots from brute forcing a user account.

- Web Application Firewalls (WAFs) – Payoneer uses both cloud-based and in-house WAFs to detect bots and prevent them from reaching our site.
- Bot-locating software – Payoneer uses software that tracks bot activity on our website according to such factors as typing speeds and mouse movements. In addition, we’re able to obfuscate password fields in web browsers to prevent bots from recording user passwords.
- Duplicate-site tracking – One of the methods attackers use to execute an ATO involves duplicating a site on a different domain name. A social engineering attack is then used to fool users into visiting the fraudulent site and entering their login details. We use advanced software to track duplicate sites, and after verifying that they are indeed fraudulent, take them down.
- Proactive user-account searches – Payoneer uses multiple cyber-intelligence services to proactively search both the clear and dark web for compromised customer account details. If a user’s login information is found, they are immediately notified and their password is changed.
1.The Gatekeeper: Adaptive Authentication
Adaptive authentication is an intuitive user verification system that evaluates risk factors, e.g., country, IP address and transaction size to flag any account abnormalities. After detecting activity that might signal an ATO, the system issues additional identification steps, such as 2SV and security questions, to ensure account security. Our threat detection system uses the latest statistical machine learning technology. This allows us to adapt and record new threats in real-time, always staying a few steps ahead of the hackers and ensuring complete data protection for our users.2. The Selector: Rule-Based Monitoring
Our rule-based monitoring engine is a backend tool that uses predefined rules to identify suspicious behavior in a user’s account. Once a rule is triggered, our forensic analysts can investigate the situation to determine if an account has been taken over. For example, an abnormally large account transfer, especially to a new Payoneer account, is likely to trigger our rule engine and lead to an investigation. If an ATO is then identified, account activity is suspended immediately and the account owner is notified.3. The Protector: Risk Models and Behavior Profiling
We use complex risk model and behavior profiling programs to analyze suspicious user transactions. The information we get from these analyses is then used to predict malicious future behavior that might signal an account takeover. For example, our risk models consider data related to suspicious behavior, such as an unusual number of cross-border payments to a specific country or high transaction volumes from a new device, and uses it to flag accounts displaying the same behavior.4. The Failsafe: Customer Feedback
We know that no matter how advanced the technology we use, there is still no substitute for human intuition. That’s why we keep a constant open line of communication with our users—doing so allows us to rapidly detect suspicious account activity, which we can then flag and apply to the steps outlined above. ATO is an inherent threat that requires proactive and innovative mitigation steps on the parts of both users and service providers. While we’re unable to disclose all of our security measures here, we can say that our mitigation methods actively block malicious actors and bots from accessing sensitive data, while ensuring that we’re able to immediately address any suspicious activity to secure your account. It is for this reason, and many more, that some of the world’s leading digital brands, including Amazon, Airbnb and Google, together with millions of SMBs worldwide have put their trust in Payoneer, knowing that account security is always at the front of our mind. If you have any further questions about account security, please contact your customer success manager or our customer care team and we’ll be happy to help. * Currently, 2-step verification is available in Europe and certain other countries, and is expected to be fully rolled out in the coming months. Editor’s Note: The original post was updated on 13.02.2020 for accuracy and comprehensiveness.Related resources
Latest articles
-
How to simplify payment operations with Payoneer’s automation feature
Save time, reduce costs, and eliminate errors with Payoneer’s new payment automation feature.
-
How to prevent online payment fraud as an SMB
Prevent online payment fraud by overcoming challenges like phishing, fake accounts, and account takeovers (ATO) with enhanced security features from Payoneer.
-
Amazon Fees & Policy Updates 2024
Amazon regularly makes planned updates to fees and policies that may impact Payoneer customers that sell on Amazon. To keep Payoneer customers informed regarding upcoming and past updates, we’re providing a list of known changes to Amazon fees and Policy updates.
-
How Payoneer’s target exchange rate feature will help you save more on bank withdrawals
Boost savings with Payoneer’s target exchange rate feature.
-
Navigating phishing attacks: A guide to keeping your Payoneer account secure
Keeping your funds safe is our number one priority at Payoneer. While phishing attempts can happen, arming yourself with knowledge is key to keeping your data and money safe
-
Zoho Books and Payoneer integration guide
Learn how to seamlessly integrate Payoneer with Zoho Books. Follow our step-by-step guide to connect your accounts, create invoices, and manage payments efficiently. Optimize your financial operations today!














